Computer programs used to search for cyber vulnerabilities are penetration testing techniques.
Some specific advantages are given by each application on this list. A simple comparison allows you to decide if the program is the right option for your organization. Let's explore to find the latest choices for security apps on the market.
What is Penetration Testing
Penetration testing, also called as pen testing, ensures that information security experts use security bugs in a computer program to find and take advantage of them. These specialists, often classified as white-hat hackers or ethical hackers, make things simpler by detecting attacks by cyber attackers known as black-hat hackers in the modern environment.
In reality, performing penetration testing is equivalent to hiring experienced analysts to conduct a safe facility security breach to figure out how it could be achieved by actual criminals. Businesses and companies are using the results to make the frameworks more stable.
Need of Penetration Testing
Pen testing often demonstrates that where and how the system might be abused by a malicious intruder. This helps you to eliminate any vulnerabilities before a real attack happens.
According to a recent Optimistic Technologies study, every other business has vulnerabilities that can be abused by attackers. Pen testers have been able to violate the company network and enter the network in 93 percent of instances. Four days was the average time taken to do so. An untrained hacker would've been able to access the internal system at 71 percent of the firms.
Working Functionality of Penetration Testing
Firstly, penetration testers need to think about the operating systems that they are going to try to hack. Then, to identify vulnerabilities, they usually use a collection of software tools. Penetration monitoring can also include hacking risks from social engineering. By entrapping a member of the group into having access, testers will attempt to obtain access to a device.
Penetration testers also provide company with the outcomes of their checks, and that is responsible for introducing improvements that either fixes the vulnerabilities or minimize them.
Classification of Penetration Tests
Penetration testing contains the following essential types that are listed below.
- Blind Tests
- White box Tests
- External tests
- Double-blind tests
- Internal Tests
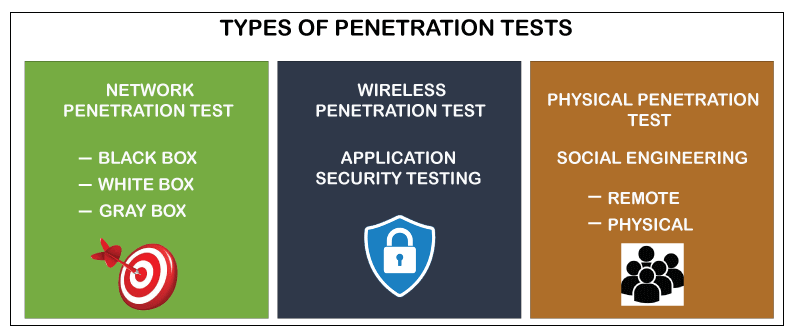
Let's discuss each one in detail.
Blind Tests
The Companies offers penetration testers with little security details about the device being exploited in a blind test, referred to as a black-box test. The aim is to find vulnerabilities that wouldn't ever be discovered.
White box Tests
A white box test is one where companies offer a range of security details related to their structures to penetration testers to help them improve vulnerabilities.
External Tests
An external test is one where, globally, penetration testers aim to identify vulnerabilities. They are carried out on macro environment-facing software such as domains because of the existence of these kinds of testing.
Double-blind Tests
A double-blind test that is also defined as a covert test is one where sensitive data is not only given to penetration testers by companies. They still may not make the assessments known to their own information security experts. Traditionally, such experiments are strongly regulated by those conducting them.
Internal Tests
An internal examination is one where the examination of penetration exists within the boundaries of an entity. Typically, these checks concentrate on the security weaknesses of which full advantage could be taken by anyone operating from inside an organization.
Best Penetration Testing Tools and Software
1. Wireshark
Typically named as Ethereal 0.2.0, with 600 contributors, Wireshark is an award-winning network mapper. You can catch and analyze data packets easily with this program. The tool is open-source and is compatible with Windows, Solaris, FreeBSD, and Linux, among other frameworks.
Key Points
- It offers both offline review and options for live-capture.
- Its locating intermediate nodes help you to discover new characteristics, including the protocol of the source and destination.
- It includes the opportunity to inspect the smallest information in a network for operations.
- It contains optional colouring rules for fast, intuitive analysis and are added to the pack.
2. Netsparkar
A common automated application server for penetration testing is the Netsparker vulnerability scanner. From cross-site request to SQL injection, the program can recognize anything from it. This tool can be used by designers on blogs, web infrastructure, and web services.
The platform is efficient enough to simultaneously search anything from 500 to 1000 software applications. With attack tools, verification, and URL rewriting guidelines, you will be have the ability to modify the security scan. In a read-only manner, Netsparker takes advantage of vulnerabilities spots dynamically. Exploitation proof is made. The effect of vulnerabilities can be viewed instantly.
Key Points
- It can search the web-based applications for 1000 + in less than a day!
- For teamwork and easy discoverability of results, you can add several teammates.
- The Advanced scanning reduces the need for a small set up.
- It can search for SQL and XSS bugs in software applications that are hackable.
- You can create the Legal application of the web and reports of regulatory requirements.
- It has Proof-based screening technology to ensure precise identification.
3. BeEF
This is a guide for pen testing and is perfectly suited to a search engine for testing. Applied to fight internet-borne attacks and could help mobile customers. BeEF refers for Platform for Browser Manipulation and uses GitHub to find problems. BeEF is designed to determine vulnerabilities outside the range of the web client and the network. Rather, than the context of only one reference, the search engine, the framework would look at detectability.
Key Points
- To verify the security infrastructure, you might use client-side known vulnerabilities.
- It helps you to connect with more than one search engine and then begins specific packages with commands.
4. John The Ripper Password Cracker
One of the most common flaws is passwords. To capture information and access sensitive systems, hackers can use credentials. For this reason, John the Ripper is the indispensable tool for password guessing and offers a variety of systems. The pen vulnerability scanner is a free software to use.
- It automatically detects various variations of passwords.
- It also discovers inside databases password vulnerabilities.
- For Linux, Mac OS X, Hash Suite, and Hash Suite Droid, the premium edition is available.
- A personalized cracker is included.
- It helps people to discover online documentation. This provides a description of improvements between variants that are distinct.
5. W3af
In all software development, W3af custom application intrusion and review platforms are based on identifying and exploiting defects. For attack, audit, and discovery, three kinds of plugins are given. Then, the software moves these on to the assessment instrument to evaluate for security flaws.
Key Points
- For professionals, it is easy to use and strong enough, even for developers.
- Automated HTTP request creation and existing HTTP requests can be accomplished.
- It has the ability to configure to function as a proxy for MITM.
6. Metasploit
Metasploit is the world's commonly utilized system for vulnerability assessment optimization. Metasploit allows technical experts to validate and manage safety evaluations, enhance visibility, and arm and inspire defenders to remain in the game a point ahead.
It is helpful to test security, and to find vulnerabilities, to build up a defense. This tool, an open standard program, will enable a system-administrators to crack in and recognize critical flaws. To build up their abilities, novice hackers use this guide. The tool offers social engineers with a way of replicating websites.
Key Points
- It is convenient to use with a scrollable given platform and command-line interface.
- Brute-forcing guides to launch systems to bypass urbanization and modernization, spear spyware, and recognition, an OWASP vulnerability testing app.
- It collects the data from testing for more than 1,500 exploits.
- Meta Modules for experiments of network connectivity.
- This can be used inside infrastructure to discover older vulnerabilities.
- It is also accessible for Mac OS X, Linux and Windows.
- It can be used on servers, software, and channels.
7. Acunetix Scanner
Acutenix is an interactive platform for testing that you will use to execute a penetration test. The technique is capable of evaluating complex management reports and compliance problems. A number of network vulnerabilities can be addressed by the app. Acunetix is also able to include bugs that are out-of-band.
The comprehensive tool combines with WAFs and the widely valued Error detectors. Acunetix is one of the specialized cross-site requests and SQLi testing in the sector, with a high accuracy rate, which includes sophisticated automated XSS detection.
Key Points
- Over 4500 vulnerabilities are protected by the tool, which involves SQL injection and XSS.
- The Login Pattern Recorder is simple to implement and tests sections covered by passwords.
- AcuSensor Technology, Tools for Automatic Penetration, and Built-in order to strengthen and allow abatement, vulnerability assessment streamlines black and white box testing.
- Hundreds of millions of websites can be ransacked without interruption.
- It can operate locally or via a solution in the cloud.
8. Aircrack
Aircrack NG is configured to hack vulnerabilities inside the wireless connections by trapping incoming packets for an efficient protocol to be exported for analysis through word documents. Although the program seemed to have been discontinued in 2010, in 2019, Aircrack has modified again.
This tool is enabled on multiple OS and WEP dictionary-based attack support frameworks. Especially in comparison to many other penetration tools, it provides an increased detection performance and supports several devices and drivers. The suite is responsible for using a credential dictionary and mathematical techniques to crack into WEP after obtaining the WPA handshake.
Key Points
- It is compatible with Solaris, Linux, Windows, OS X, FreeBSD, NetBSD, and OpenBSD.
- To retrieve packages and export data, you will use this method.
- It is intended for wi-fi system testing as well as driver proficiency.
- It focuses on various security fields, such as an attack, surveillance, testing, and cracking.
- In terms of intrusion, you can de-authenticate, establish a fake wireless network and replay attacks.
9. Burp Suite Pen Tester
The Burp Suite for programmers has two separate editions. The free version offers appropriate and essential tool for testing operations that are needed. Or, when you need extensive penetration testing, you can go for the second version. For testing web-based applications, this tool is perfect. Tools for mapping the tack substrate and analyzing transactions between the browser and endpoint servers are available.
Key Points
- It is suitable for web-based software scrolling automatically.
- Mac OS X, Linux, and Windows are accessible in this tool.
10. Kali Linux
A Linux operating system used for vulnerability assessments is Kali Linux Specialized Penetration Testing Program. This is the perfect instrument for both extracting and password snipping, many analysts claim. However, to achieve the most of the advantages, you might need experience in both TCP / IP protocols. Tool descriptions, edition management, and meta-packages are supported by an open-source project, Kali Linux.
Key Points
- You will use this technique for brute-force attack password cracking with 64-bit assistance.
- To evaluate the security skills of cybersecurity professionals, Kali uses a live image configured into the RAM.
- Kali Linux contains 600 hacking methods that are ethical.
- Multiple vulnerability assessment security tools, web applications, data collection, wi-fi attacks, reverse engineering, cracking passwords, forensic tools, web services, imitating, sniffing, trafficking tools, and hacking device are obtainable.
- It has fast compatibility with other tools, include Wireshark and Metasploit, for penetration testing.
- BackTrack offers testing, forensic analysis, and sniffing tools for Wireless Lan and LAN vulnerability analysis.
11. Ettercap
The Ettercap software is intended to avoid attacks by a person in the Centre. You will be able to generate the packages you need and perform certain tasks using this tool. The program can submit illegitimate frames and entire technologies via other options that are more complicated.
Key Points
- This method is suitable for deep sniffing of packets as well as LAN tracking and checking.
- Passive and active defense deconstruction is provided by Ettercap.
- The internal control system can be done on the fly.
- For both channel and client evaluation, the tool also offers configurations.
12. Nessus
Over twenty years, Nessus is often used as a privacy vulnerability scanning tool. Twenty-seven thousand leading organizations use the program. Including over 45,000 CEs and 100,000 extensions, the app is among the strongest testing tools and services. Optimal for analyzing IP addresses, domains and conducting critical searches for data. You will be eligible to use this in the frameworks to identify 'weak spots.'
This tool is easy to use and provides reliable testing, and presents an analysis of the vulnerabilities of the network at the click of the mouse. Searches for known vulnerabilities, poor passwords, and data corruption errors by the pen test program.
Key Points
- This tool is optimal for the location and detection of faulty patches and vulnerabilities.
- Per 1 million tests, the device has just .32 errors.
- This tool helps you to customize files containing vulnerability forms, can be generated by the plugin or server.
- The tool provides preference mitigation in addition to make sure software, device scanning, and cloud infrastructure.
13. Zed Attack Proxy
OWASP ZAP is a tool of OWASP group. It is suitable for architects and programmers that are acquainted with penetration testing. The campaign began in 2010 and is being enhanced every day. ZAP executes in a multi-platform strategy that supports a proxy between the domain and the server.
Key Points
- Four modes are available with customizable options.
- JAVA 8 + is necessary for the Windows or Linux platform to access ZAP.
- Getting Started (PDF), Introduction, online help, professional associations, and StackOverflow are extensively supported pages.
- People via program code, Wiki, Developer Community, Crowdin, OpenHub, and BountySource will explore more about Zap growth.
14. SQLmap
SQLmap is a Database SQL Injection Control Tool. It also enable MySQL, SQLite, Sybase, DB2, Access, MSSQL, PostgreSQL database platforms. SQLmap is open-source and streamlines the mechanism of manipulating the application server and bugs for the Attack vector.
Key Points
- This tool allows you to Detect exploits and monitor them.
- It offers assistance for all aspects of injection: Union, Time, Stack, Error, Boolean.
- It executes a command-line interface and can be configured for Linux, Mac OS, and Windows operating systems.
15. Cain and Abel
Cain & Abel is suitable for penetration for the acquisition of network controls and credentials. To detect the vulnerability, the tool makes the utilization of network sniffing.
Key Points
- Utilizing the network sniffers, cryptographic algorithms threats, and brute force, the Windows-based framework can restore passwords.
- It is Superb for missing password restoration.
16. Wapiti
Wapiti is a security tool for programs that enables black-box testing. Checking the black box tests web-based applications for possible exposures. Websites are checked at the time of the black box testing procedure, and the tested data is implanted to search for any failures in protection.
Key Points
- With the help of command-line application interface, professionals may find ease-of-usability.
- Wapiti detects file exposure glitches, XSS Intrusion, Database transfusion, XXE injection, Command Execution mitigation, and vulnerable .htaccess settings that are easily evaded.
17. Social Engineering Tool (SET)
The key objective of the tools and techniques is social engineering. Living beings are not the aim of penetration testing beyond purpose and emphasis.
Key Points
- This tool presented at prominent cybersecurity events, include ShmooCon, Defcon, DerbyCon, and is a vulnerability assessment industry norm.
- There have been over 2 million downloads of Package.
- An open-source test system is developed to prevent social engineering.
18. Hydra
When you need to break an encrypted password, including an SSH or FTP account, IMAP, IRC, RDP and several others, John the Ripper's accomplice, Hydra, plays a role. Place Hydra at the system that you'd like to hack since you like, pass a set of words, and squeeze the trigger. Services like Hydra are a demonstration of why, during a couple of password attempts, rate-limiting password tries and unplugging users can be efficient preventive measures toward the attackers.
19. Hashcat
The self-proclaimed "the quickest and most sophisticated password protection tool in the world" may not always be humble, but the hashcat folks sure know its value. John the Ripper is offered a challenge for his money by Hashcat. It is the perfect solution-to pen- testing method for cracking hashes, and hashcat enables several forms of brute force attacks through password cracking, like a dictionary and disguise attacks.
Pentesting typically entails hashed credentials being exfiltrated, and manipulating those passwords involves turning a software such hashcat unleash on them offline in the expectation of at least a few passwords being guessed or brute-forced.
On a standard GPU, Hashcat performs perfectly (sorry, Kali VM users). Legacy hashcat also facilitates CPU hash hacking, but it warns users that it is marginally slower than integrating the computational capabilities of the graphics card.
Advantages of Penetration Testing Tools
Here, some advantages of pen-testing tools are defined below.
1. Arrangement and Detection of Security Threats
A penetration test calculates the capability of the organization to secure their apps, servers, users and data sources from international and domestic attempts to avoid its security measures in order to obtain restricted or unsanctioned access to secured properties. The pen test result confirms the danger posed by specific security problems or defective systems, enabling abatement initiatives to be arranged by IT management and intelligence analysts.
2. Subvert the channel failure intensity
Recovering from a security flaw is costly. IT rescue station, retention measures, consumer security, commercial-grade, reduced sales, decreased employee productivity, and frustrated trade representatives can be included in recovery. Penetration testing helps a company to prevent these financial difficulties by recognizing and resolving risks constructively before data breaches or attacks occur.
3. Meet the needs of tracking and mitigate penalties
The ultimate monitoring/implementation aspects of activities such as HIPAA, SARBANES-OXLEY, and GLBA are discussed by IT agencies, as well as the monitoring needs to be acknowledged in the federal NIST / FISMA and PCI-DSS directions. The detailed reports provided by the vulnerability scanners will help organizations escape significant non-adherence consequences and allow them to demonstrate continuing due diligence in evaluators by retaining the appropriate safety controls for auditors.
4. Service delays and security problems are costly
Security vulnerabilities and the corresponding performance disturbances in service providers can result in crippling economic harm, damage the credibility of an enterprise, decimate customer loyalties, elicit negative attention, and impose unexpected financial penalties. Frequent recruitment in penetration testing by the company prevents these expenses.
Checking penetration enables the company to prevent invaders of the infrastructure. It is safer for the company to protect its protection promptly than to suffer drastic failures, both in terms of its brand value and its financial stability.
5. Secure brand recognition and corporate image
Only a single instance of stolen consumer data may kill the reputation of a business and affect its end result negatively. Penetration testing can help an entity eliminate data accidents that can place the integrity and reliability of the business at risk.



0 Comments